In a startling revelation, the RockYou2024 wordlist has exposed billions of passwords, sparking concerns and headlines across the globe. This massive data leak is one of the largest in history, yet there are compelling reasons why you shouldn't be overly worried. Here’s a deep dive into what happened, its implications, and why panic isn't necessary.
RockYou2024 Leak: What Happened?
RockYou2024 is a compilation of passwords gathered from various previous data breaches. This new wordlist includes over 8.4 billion entries, a staggering number that highlights the sheer volume of compromised credentials over the years. The name "RockYou2024" is a nod to the infamous RockYou data breach of 2009, where 32 million passwords were exposed due to poor security practices.
Why You Shouldn’t Panic
Before we get into all the specifics, let me give you a background on how wordlists are used. As a former ethical hacker, I utilized password lists such as the RockYou wordlist from 2009 on various engagements. One of the most popular engagements is when a company hires you to do a password audit on the employees. It is usually to make sure that the employees and the company are in compliance with their password policy.
The typical scenario is when you export the password database from the company domain controller, use a password list, and attempt to crack the passwords. If you were successful, you would send the list to the manager, and they would meet with employees or teams to go over the results…so don’t make passwords about your boss or the company you work for.
Another example is if I was attempting to crack a password. This could be a password for a file or a password for an account. If you are someone like me, I do not have the income to support a password-cracking device. I had to use whatever processing power my laptop had at the moment. Does this mean that I would achieve a “PWN” status every time I used the RockYou wordlist? No.
I disliked using wordlists because it took time, patience, and a special piece of hardware known as a “Cracking rig” to crack passwords if they were obtained. If you were successful at cracking passwords, accessing infrastructure from outside an organization that was utilizing multifactor authentication would alert the employee when you attempt to log in.
Instead of cracking passwords, one of the most used tactics today is buying stolen credentials from the dark web. Why go through all the work of cracking passwords, when they can be bought for a decent price? Cybercriminals use various methods to gather stolen credentials and sell them to the highest bidder.
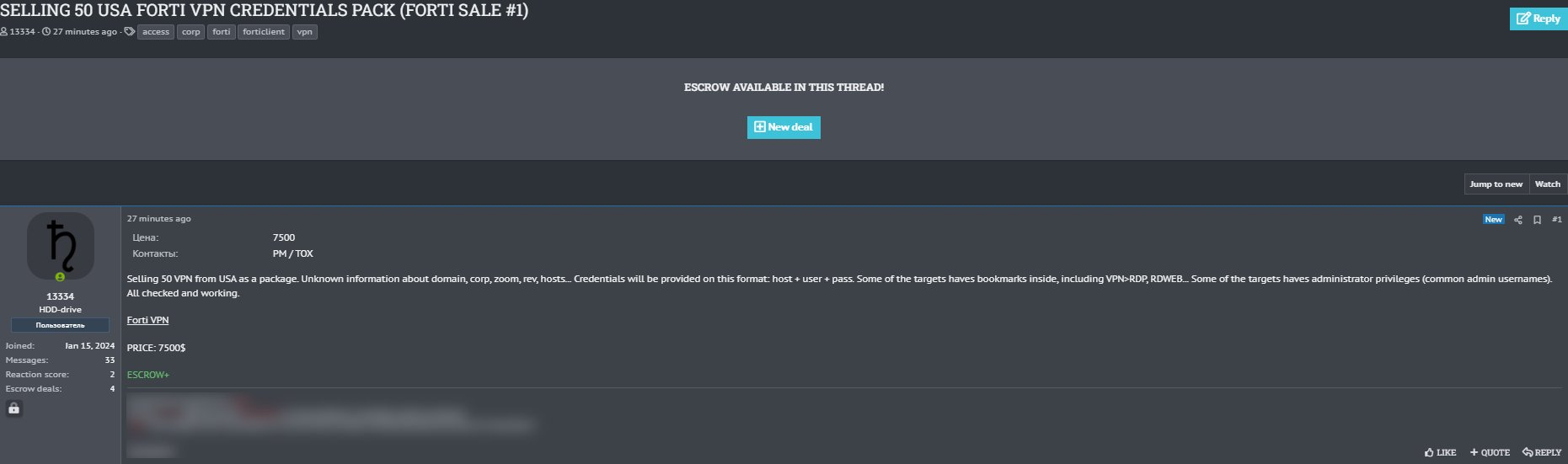
Another method that a cyber-criminal will use if they are inside your network, is “Pass the hash.” A Pass-the-Hash (PtH) attack is a technique where an attacker captures a password hash (as opposed to the password characters) and then passes it through for authentication and lateral access to other networked systems.
With this technique, the threat actor doesn’t need to decrypt the hash to obtain a plain text password. This means that I have no use for the RockYou2024 wordlist and only need to pass the password on various network subnets to see if the user account has access. Work smarter…not harder.
Why You Shouldn’t Be Overly Worried About RockYou2024.
1.) Old Data, Limited Usefulness: The vast majority of the passwords in the RockYou2024 wordlist are old. They are from previous breaches and have likely been changed by now. Most users update their passwords regularly, especially after a breach notification. So, while the number is alarming, the actual risk to current accounts is diminished.
2.) Increased Awareness and Security Measures: Over the years, awareness about cybersecurity has grown significantly. Users are more educated about the importance of strong, unique passwords and the use of password managers. Additionally, many online services have implemented stronger security measures, such as two-factor authentication (2FA), making it much harder for attackers to exploit leaked passwords.
3. Password Managers and Unique Passwords: The adoption of password managers has helped users create and store strong, unique passwords for each of their accounts. This practice limits the potential damage from any single breach. Even if one password is exposed, the rest of the user's accounts remain secure. There are cases where password managers get compromised like LastPass, but they are very useful.
Steps to Enhance Your Security
While the RockYou2024 leak may not be cause for panic, it's always a good idea to take proactive steps to secure your online presence:
1. Use Strong, Unique Passwords: Avoid using common or easily guessable passwords. Utilize a combination of letters, numbers, and special characters to create strong passwords. A password manager can help generate and store these passwords securely.
2. Enable Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring a second form of verification, such as a text message or authentication app code. This makes it significantly harder for attackers to gain access to your accounts, even if they have your password.
The RockYou2024 password leak is a reminder of the ongoing challenges in the realm of cybersecurity. However, by understanding the nature of the leak and taking proactive steps to secure your accounts, you can significantly reduce your risk. Awareness, vigilance, and modern security measures are your best defense against potential threats in the digital age.
So, while the headlines may be alarming, there's no need to panic. Instead, use this opportunity to reinforce your online security habits and stay one step ahead of cybercriminals.

